Assima = Faster Digital Adoption
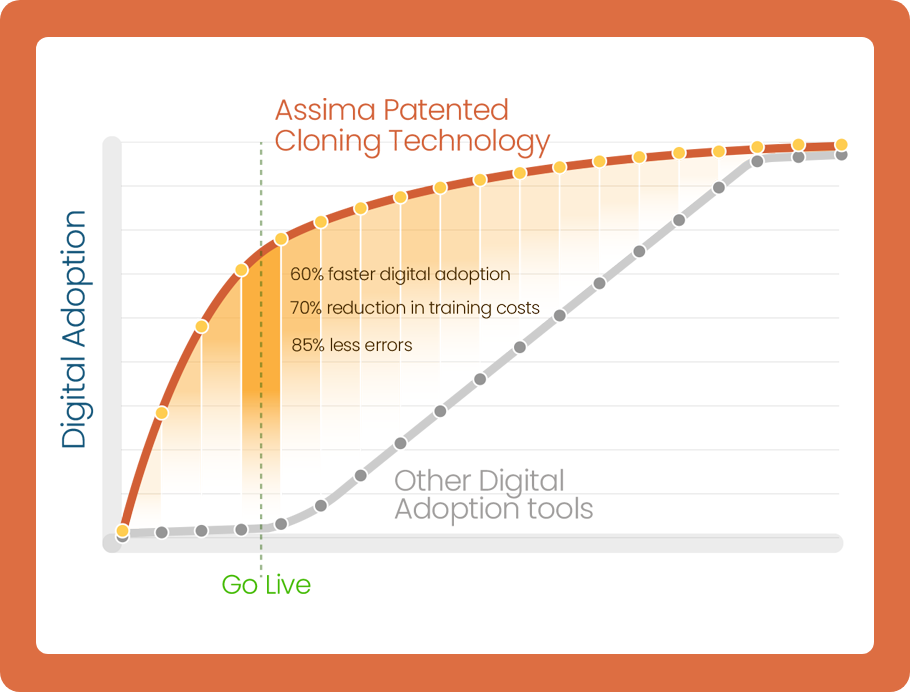
World’s leading companies unlock technology ROI up to 50% faster and lower training costs by 70% with Assima, the world’s #1 systems training platform.
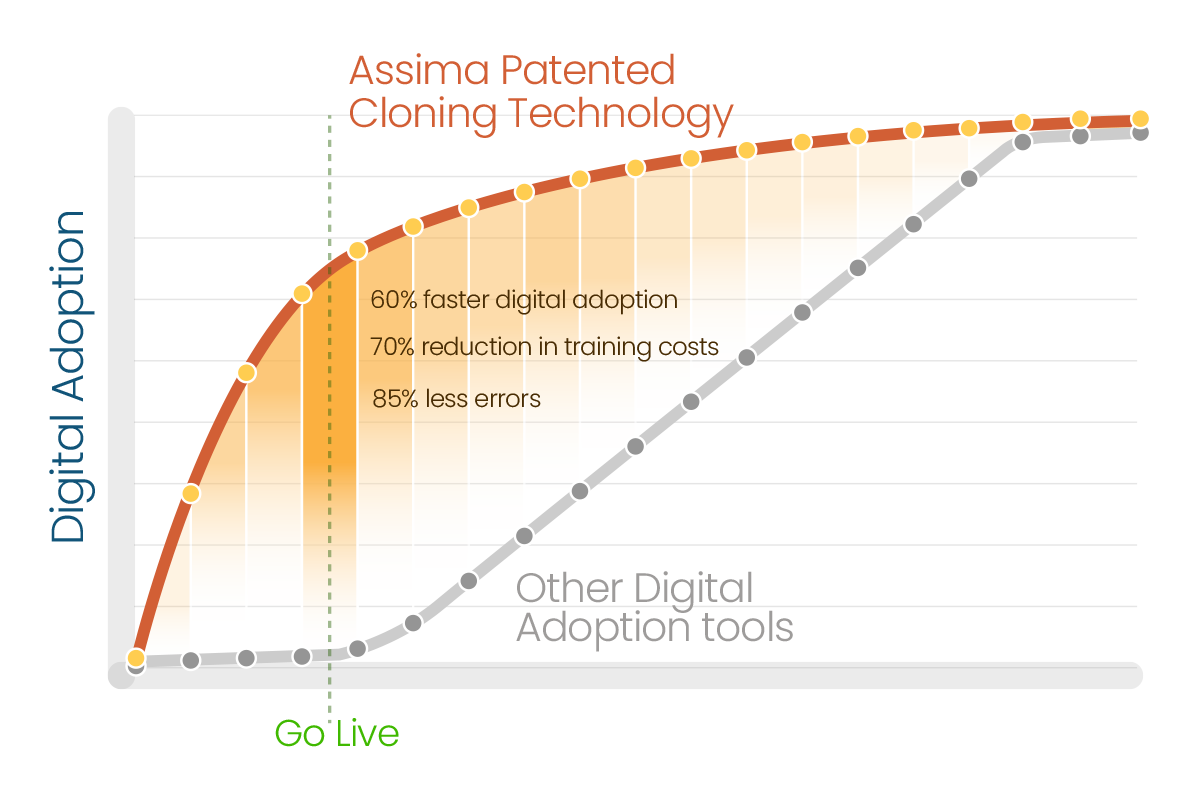
Powered by the World’s Only 4x Patented Cloning Technology
The #1 Systems Training Platform
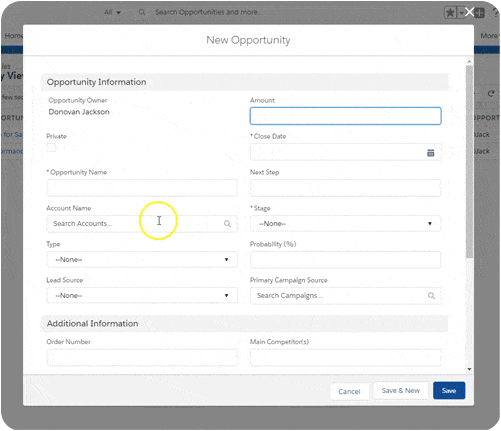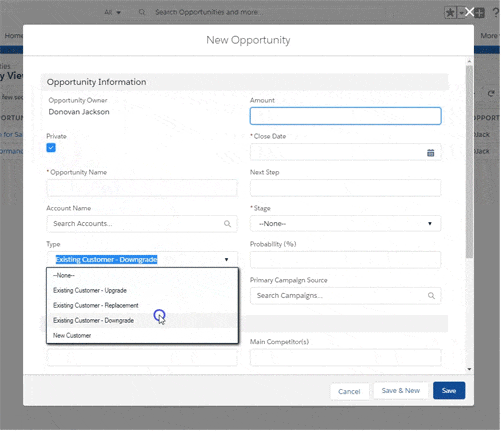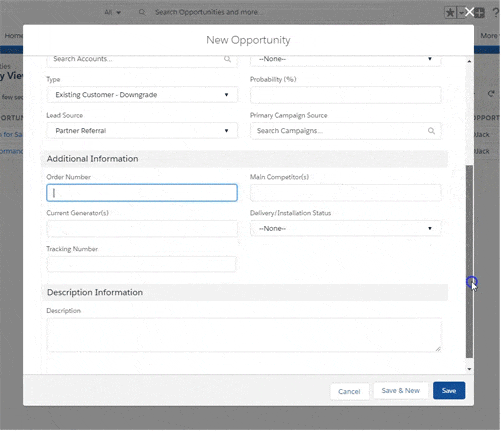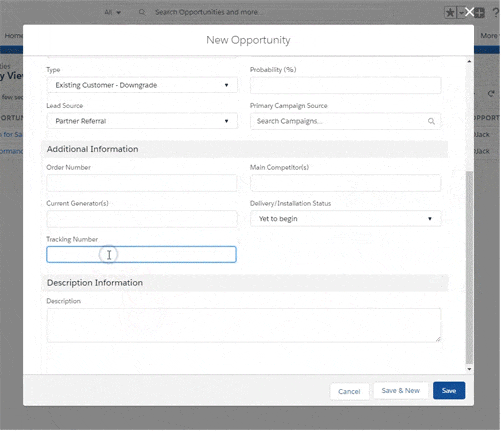
Unlike any other solution on the market, Assima does not deliver systems
training as static images. The output is a fully interactive interface that you can
edit at will.

For Content Creators and For End-Users
Edit anything on your screen and mass replace data across lessons. Click, scroll, use dropdown menus, enter the data into fields – in any order, just like in the real system.
Powered by the World’s Only 4x Patented Cloning Technology
The #1 Systems Training Platform
Unlike any other solution on the market, Assima does not deliver systems
training as static images. The output is a fully interactive interface that you can
edit at will.
For Content Creators and For End-Users
Edit anything on your screen and mass replace data across lessons. Click, scroll, use dropdown menus, enter the data into fields – in any order, just like in the real system.
The #1 Systems Training Platform

Make employees proficient in record time.
Maximize technology ROI.


Build a digitally fit workforce.

Make employees proficient in record time.
Maximize technology ROI.


Build a digitally fit workforce.
A 20-Year Track Record No One Can Match
training costs
onboarding
delivery
help desk calls
Deliver The Most Realistic And Impactful Learning Experiences
Assima creates hyper-realistic simulations of any application so you can train your employees the way humans learn best: practicing, solving problems, making mistakes, and building confidence. It’s the closest thing to training in a live system without any risks.
It’s also the only cost-effective way to deliver realistic training for business processes running across multiple applications.


Create The Only Training Assets That Move With Your Business
Your training needs to be constantly reworked to reflect new updates, regulations, compliance.
Unlike every other solution on the market, Assima creates editable clones of your systems so your training can be updated in a few clicks – reducing rework by 90%.
New fields, pulldown menus, buttons, entries can be added, resized, and removed at will – without re-capturing a new set of screenshots.
Keep Up Stay Ahead of The Pace of Change
Leave everyone in the dust. Future-proof your workforce by reflecting updates to your training even before your production environment is complete.
Your employees now have more time to train and always practice with the latest features.
For new software rollouts, accelerate adoption by delivering a realistic version of your software to your business people months before go-live.


Ditch Expensive IT Training Environments
Even if a sandbox came for free with your software, the costs and time to configure and maintain multiple environments for training or localization represent a tremendous and needless expense.
With Assima, you can unlock substantial savings by creating simulations that grant you the realism of a dedicated training environment but without the maintenance and frustrating data refreshes.
Discover Assima’s Total Digital Adoption Framework
Here’s the biggest myth in the industry: in-app overlays or performance support alone is enough. It’s actually dangerous and puts your customers, teams, and data at risk.
Solution: Instead of being overwhelmed and vulnerable to costly mistakes “in the flow of work”, our proven approach is designed to empower your employees with a safe environment to practice, build muscle memory and become fully ready on day one.


Learn How Our Customers Onboard Faster and Reduce Costs with Assima
“Here was a system that would allow me to train new staff without the astronomical cost of building and maintaining a training client.”






Fundamentally Change For The Better with Assima
- Get expert advice tailored to your use cases and industry
- Discuss your environment & pricing options
- Take the best path to get started